This story was updated on Monday July 14, 2025 to reflect new information from Abode, which alerted us to its dedicated security contact and shared its bug bounty program.
Consumer Reports (CR) has found that one year after it first started investigating, more smart home device manufacturers are making it easier for security researchers to let them know about security vulnerabilities.
For the second year in a row, CR has surveyed 75 smart home device makers to understand if they provide an easy way for a researcher to report potential cybersecurity problems in their product. This year saw 11 additional companies add security contacts to their web site, leaving only 10 companies, or 13 percent, that don’t have a dedicated security contact.
This is down significantly from the year prior when 21 companies (28%) didn’t have an easily found security contact. Several of the companies confirmed they added a security contact after we published our research.
Having an easy-to-find security contact is important because vulnerabilities in the software or hardware associated with connected devices can harm consumers. Vulnerabilities can lead to attackers accessing the device to to spy on users or seeing data such as passwords. In addition to violating user privacy, vulnerabilities can also lead to malicious actors taking over smart home devices to use them in other attacks. As the smart home industry has matured, we rarely hear about companies passing along Wi-Fi passwords in plain text, but there are still plenty of vulnerabilities that researchers can find.
“As a member of a team that submits an average of 20 vulnerability disclosures each year, having a dedicated security contact not only demonstrates that security is not an afterthought, but it also can transform a potentially ignored warning into an effective communication channel with a team equipped to escalate and resolve them,” says Steve Blair, Privacy and Security Test Program Leader at CR.
A New Focus on Vulnerability Disclosure Programs
Of course, letting a company know about a potential vulnerability is just the first step. CR also likes to see companies lay out their process for dealing with reported vulnerabilities. That’s why we also look for companies to have a formal vulnerability disclosure policy (VDP). These programs explain how security researchers can report a vulnerability to a company and describe how the company plans to research and remediate the vulnerability.
A good VDP will dictate how a security researcher should share their findings, and explain how the company typically handles a vulnerability report. Ideally, the VDP should lay out how long the researcher will take to hear from the company after making a report and how the company would like to handle responsible disclosure of the vulnerability.
Vulnerability disclosure programs also lay out the company’s idea of ethical behavior for security researchers and assure researchers that if they follow the guidelines, the company will not sue. Some give time frames on how long it will take to mitigate a vulnerability.
This is such an accepted and core tenet of good cyber hygiene that it is part of National Institute of Standards and Technology (NIST) recommendations for consumer IoT products, and will likely be required for companies seeking to get certified to use the U.S. Cyber Trust Mark. The Cyber Trust Mark will indicate that a device meets certain security standards after undergoing testing by a third-party lab.
CR discovered that 51 of the 75 companies surveyed had formal vulnerability disclosure policies (VDPs) in addition to their dedicated security contacts, which was the same as last year. It’s clear that our work in the next year will be to get the 10 companies listed below to add a dedicated point of contact for security researchers and encourage the 25 companies without formal VDPs to adopt one. Unsurprisingly if a company did not have a dedicated security contact, they did not have a VDP either.
The Smart Home Security Laggards
The companies without a dedicated security contact and without a VDP are:
- Aerogarden
- Genie
- Hydrow
- Level
- Lockly
- Orbit/B-Hyve
- SleepNumber
- Tempo
- Tonal
- Vizio
The inclusion of Vizio, a smart TV manufacturer, on this list is concerning. Smart TVs have a lot of computing power and are often a popular target for botnets, so the lack of a dedicated contact to report vulnerabilities means that unpatched issues could result in a powerful botnet. And any consumer buying a security system likely expects that the company’s focus on security would extend to the digital world as well. After all, if a hacker can access a security system, then it’s not very secure.
The list of companies lagging in this area also includes several connected fitness devices such as the Hydrow rower, and the Tonal and Tempo gyms — some of which collect a lot of information a user might want to keep locked down. Also of concern is the inclusion of The Overhead Door company, which makes the Genie brand of garage door openers, and two connected lock makers Lockly, and Level. Last year, Level was acquired by Assa Abloy, which does have both a dedicated security contact and a VDP for the entire company including Kwikset locks, but it’s not clear if the Level acquisition is covered by those terms yet, and Assa Abloy and Level did not respond to our questions about security contacts and vulnerability disclosure policies.
Most of the companies listed above didn’t respond to repeated requests for comment about their security contacts or processes for managing vulnerability reports. However, Sleep Number did say that while it does not have a dedicated security inbox, phone line or website, it does have “an internal escalation process to raise technical and cybersecurity concerns to the right teams when they come in through our dedicated consumer support channels (phone, chat, email).” The company also lists that it has a vulnerability management program in its filings with the U.S. Securities and Exchange Commission. (Generally the difference between a vulnerability management program and a VDP is that a vulnerability disclosure program is public-facing.)
At CR we think that the public-facing aspect is important, because it makes it easier for external researchers, such as our testing team, to inform device makers when there may be a problem, and provides insights into how well a company handles such reports. CR recommends that consumers look for companies that have made clear investments in their cyber hygiene, and a dedicated security contact and vulnerability disclosure program are good metrics for such investment.
Companies that Have Made a Start
With that in mind, here are the additional 14 companies that do not have public vulnerability disclosure management programs. We hope to see them adopt such programs when we conduct this research next year.
- Abode
- Bissell
- Ecobee
- Aqara
- Delta
- Eight Sleep
- Fisher Price/Mattel
- Garmin
- Hasbro
- Kohler
- Rachio
- Vivint
- TP-Link
- Belkin Wemo/Phyn
To discover what companies had dedicated security contacts, we searched Google and the search term ”[company name] report a security vulnerability.” If the search didn’t turn up anything we scanned the site’s privacy policies, terms of service, and forums for dedicated points of contact to report bugs.
We then followed up with letters to each manufacturer, including a questionnaire designed to assess how mature their vulnerability disclosure program is. We gave companies 15 days to respond and then nudged them again via email, giving them an additional two weeks. Then we compiled the data and created this blog post. We heard from 52 of the 75 companies we contacted. In cases where the company did not respond, if there was a vulnerability disclosure policy available, we used it to fill out our questionnaire.
These Companies have Stepped Up
The following companies have both a dedicated point of contact for security researchers and a vulnerability disclosure management program.
| ADT | August/Yale | Amazon |
| Apple | Arlo | Assa Abloy (Kwikset) |
| Bosch | Chamberlain | Comcast |
| Ecovacs | Electrolux/Frigidaire | Eufy |
| Eve | Feit | GE Appliances |
| GE Sync | Google Nest | Govee |
| Hisense | IKEA | IFit (NordicTrak) |
| iRobot | Kidde/Carrier | LGE |
| Lutron | Meross | Miele |
| Moen | Nanoleaf | Owlet |
| Peloton | Reolink | Resideo |
| Robotrock | Roku | Samsung |
| Schneider Electric | Sengled | Shark |
| Shelly | Simplisafe | Signify |
| Sony | Sylvania/Ledvance | The Home Depot (Afero) |
| Trane | Tuya | Whirlpool |
| Wyze |
Delving into the Details
As part of the research, we also asked ten questions designed to understand how mature their vulnerability programs were and how they treat security researchers. Not all companies answered every one of the ten questions and many of the published vulnerability disclosure programs don’t include all of the information we were looking for, so the results only cover 52 of the companies we had information for. This was less than last year, when we had information from 56 companies.
Below are the questions that we asked and the results from the survey. We also provide information on why each of these elements are important for boosting the overall cybersecurity of consumer IoT products. We included this information in last year’s report too.

The first step in creating any form of vulnerability disclosure policy (VDP) is ensuring that reports of security vulnerabilities make it to a monitored inbox in the company, and that researchers can find this point of contact. No researcher wants to see their vulnerability report end up in a spam filter or junk folder, and no company wants to miss out on a potentially big vulnerability simply because a researcher couldn’t find out how to tell anyone at the company about the problem. However, simply having a dedicated, findable point of contact isn’t enough. A company should also have a process and resources in place to respond to security vulnerability reports. This is why we ask the following questions.

Having a dedicated point of contact for researchers to share vulnerabilities is only the first step. A strong VDP also needs to have a process in place for accepting, validating and responding to vulnerability reports. A simple acknowledgement of receipt is a good first step, but a stronger program will include a statement indicating that the company will validate the bug and issue some kind of response within a set time frame. Ideally the response will also note how long the company plans to take to remediate the problem.

As mentioned above, it’s not enough to simply accept the report of a security bug, a responsible company will let the researcher know how long it will take before the researcher hears back from the manufacturer. This step is even more important if the vulnerability is actively being exploited.

This time frame can vary. This year’s responses are trending toward a more rapid acknowledgement of reported vulnerabilities, with many of those saying that they will respond within 1 week or less, sending notifications in about three days. The Consumer Reports testing team waits two weeks to hear back from a company before publishing their ratings absent any follow-up from a manufacturer. Note that once a company responds, CR gives 90 days for a patch to be issued before publication. Another way to structure a program is Google’s Project Zero security research team, which gives a company 90 days to issue a patch and then publishes results 30 days after the patch is issued, or immediately if no patch is issued.
When a vulnerability is reported, how long does it take for your company to mitigate the vulnerability?
Companies were given the option to fill in the blank for this question, and most answers were some variation of “it depends on the severity and complexity of the vulnerability.” This makes sense. More severe bugs are often fixed faster, and more complicated vulnerabilities can take more time to mitigate. However we did see a little more than a dozen companies provide a classification system for bugs and provide a specific time frame based on the criticality of the bug.
Researchers participate in vulnerability disclosure programs for a variety of reasons, but a big reason to report a bug is to ensure that the bug gets fixed. Providing a commitment to mitigate a vulnerability within a reasonable time frame (most programs use 90 days and can also provide a 14-day grace period) shows that the company is committed to fixing the problems that researchers share with them.This ultimately protects the end users, and improves security outcomes broadly across society by eliminating weak links that can be exploited.
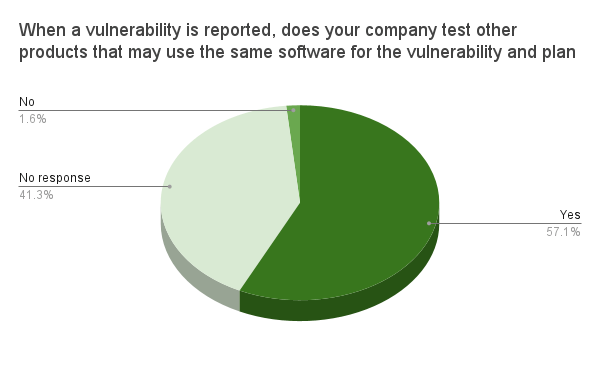
Researchers may come to a company reporting a vulnerability in a specific product. But that vulnerability might extend to other products as well. A robust vulnerability disclosure program will take steps to assess whether or not the vulnerability extends across the company’s product portfolio and then commit to fixing it.
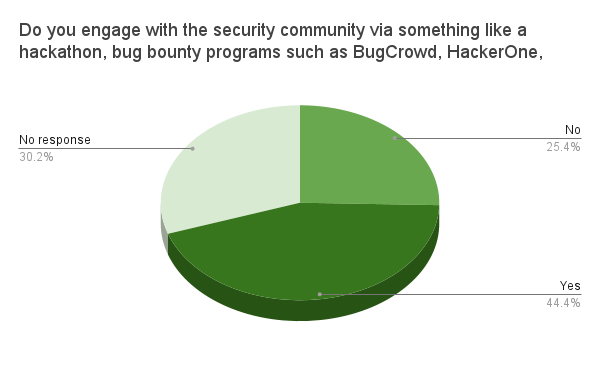
While not strictly necessary, active engagement with the security community indicates a recognition that securing connected products is an ongoing effort, and that the company wants to ensure its products stay secure. Additionally, participation in a bug bounty program where a company pays “bounties” to security researchers when they report vulnerabilities, can incentivize researchers to report found vulnerabilities as opposed to selling them to the highest bidder. Such programs also provide the exact terms of how the vulnerability disclosure program works, making it easier for researchers to see what they can expect from a program. BugCrowd and HackerOne are services that can help your company create and manage a bug bounty program.

Most VDPs provide researchers an assurance that if they tell the manufacturer about the bug, document it, and give the manufacturer time to remediate the bug, they will not take legal action against the researcher. This creates a beneficial relationship between the manufacturer and the security research community, and ensures that when people find problems, they feel safe reporting them. Having a set and delineated policy also helps ensure that researchers come to the manufacturer first when they find vulnerabilities.
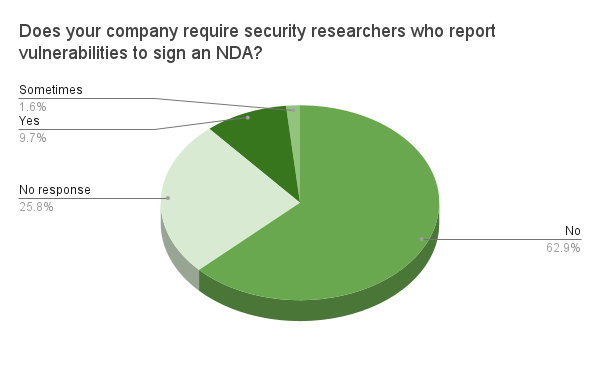
Forcing researchers to sign non-disclosure agreements will lead security researchers to avoid reporting vulnerabilities. It can signal an adversarial relationship with researchers, and also can tie researchers’ hands should the company decide not to fix a vulnerability, although ideally companies would issue security advisories after they validate reports of a vulnerability and issue a patch.

Tracking vulnerabilities over time can help a company understand how well it (or its partners) are incorporating security into their design processes, as well as ensuring that there is a record of potential vulnerabilities that can be shared with other organizations if merited. Additionally, tracking vulnerabilities helps prevent the same vulnerabilities from popping up again and again.
Next Steps and What to Look For
We’re excited at the improvement companies such as Bissell, Moen, and Mattel have made in adding dedicated security contacts. Providing this kind of information helps improve overall cybersecurity, and also tells consumers that the company cares about their safety. We’d like to see all companies that are making connected devices add dedicated security contacts.
We also urge companies to adopt formal vulnerability disclosure programs if they don’t already have them. These programs should clearly lay out how the company plans to respond to vulnerabilities by following the guidelines we list above. A robust VDP will:
- communicate receipt of a vulnerability report with the reporting security researcher within one week;
- share the company bug mitigation plan with the researcher including if they plan to mitigate it and communicate the bug to consumers;
- avoid non-disclosure agreements for researchers;
- and encourage researchers to report by pledging not to pursue legal action against those who conduct their research while following the best practices listed in the publicly available VDP.
Additionally as part of good cyber hygiene a manufacturer should create a program to track vulnerabilities over time in their products. When vulnerabilities are found, they should test other products that may use the same software for the vulnerability and plan mitigation for those products.
By implementing these policies, companies that manufacture smart devices can help make those products more secure and protect consumers from unauthorized access and ransomware attacks, and boost national security by helping keep these products from becoming part of a botnet that could be used to attack our nation’s critical infrastructure. Everyone needs to take steps to boost our cybersecurity, and at CR we’re calling on companies who make connected consumer devices to do their part.